In November 2022, the US Department of Navy (DON) released the RAISE 2.0 Implementation Guide to support its Cyber Ready initiative, pivoting from a time-intensive compliance checklist and mindset to continuous cyber-readiness with real-time visibility. RAISE 2.0 embraces a “shift left” philosophy, performing security checks at all stages of the SDLC and ensuring security issues are found as early as possible when they are faster and easier to fix.
3 Things to Know about RAISE 2.0
RAISE 2.0 provides a way to automate the Implement, Assess, and Monitor phases of the Risk Management Framework (RMF). New containerized applications can be developed using an existing DevSecOps platform (DSOP) that already has an Authorization to Operate (ATO) and meets the RAISE requirements. This eliminates the need for a new application to get its own separate ATO because it inherits the ATO of the DSOP.
There are three primary things you need to know about RAISE 2.0:
- Who must follow RAISE 2.0?
- RAISE 2.0 only applies to applications delivered via containers
- RAISE 2.0 requires all teams starting or upgrading containerized software applications to use a pre-vetted DevSecOps platform called a RAISE Platform of Choice (RPOC)
- What is an RPOC?
- RPOC is a designation that a DevSecOps Platform (DSOP) receives after its inheritable security controls have received an ATO
- A DSOP that wants to become an RPOC must follow the process outlined in the Implementation Guide
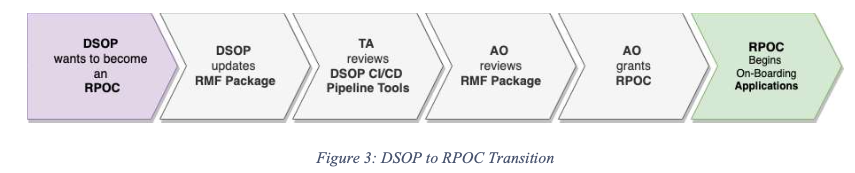
- How does an RPOC accelerate ATO?
- The containerized application will be assessed and incorporated into the existing RPOC ATO and is not required to have a separate ATO
What are the requirements of RAISE?
The RAISE 2.0 Implementation Guidelines outline the requirements for an RPOC. They represent best practices for DevSecOps platforms and incorporate processes and documentation required by the US government.
The guidelines also define the application owner's ongoing responsibilities, which include overseeing the entire software development life cycle (SDLC) of the application running in the RPOC.
RPOC Requirements
The requirements for the RPOC include standard DevSecOps best practices and specifically call out tooling, such as:
- CI/CD pipeline
- Container Orchestrator
- Container Repository
- Code Repository
It also requires specific processes, such as:
- Continuous Monitoring (ConMon)
- Ongoing vulnerability scans
- Ad-hoc vulnerability reporting and dashboard
- Penetration testing
- Ad-hoc auditing via a cybersecurity dashboard
If you're looking for a comprehensive list of RPOC requirements, you can find them in the RAISE 2.0 Implementation Guide on the DON website.
Application Owner Requirements
Separate from the RPOC, the application owner that deploys their software via an RPOC has their own set of requirements. The application owner's requirements are focused less on the DevSecOps tooling and more on the implementation of the tooling specific to their application. Important callouts are:
- Maintain a Security Requirements Guide (SRG) and Security Technical Implementation Guide (STIG) for their application
- CI/CD implementation
- Repository of vulnerability scans (e.g., SBOMs, container security scans, SAST scans, etc.)
Again, if looking for a comprehensive list of application owner requirements, you can find them in the RAISE 2.0 Implementation Guide on the DON website.

Meet Raise 2.0 requirements with Anchore Federal
Anchore Federal is the leading software supply chain security platform supporting public sector agencies and military programs worldwide. It helps RPOCs and applications owners meet RAISE 2.0 requirements by offering an SBOM management platform, container vulnerability scanner, flexible policy engine and comprehensive reporting dashboard.
Anchore Federal integrates seamlessly with CI/CD pipelines and enables teams to meet essential RPOC requirements, including RPOC requirements 4, 5, 15, 19, 20, and 24. The reporting capabilities also assist in the Quarterly Reviews, fulfilling QREV requirements 6 and 7. Finally it helps application owners to meet requirements APPO 7, 8, 9, and 10.
Continuous container monitoring in production
Anchore Federal includes the anchore-k8s-inventory tool, which continuously monitors selected Kubernetes clusters and namespaces and identifies the container images running in production. This automated tool that integrates directly with any standard Kubernetes distribution allows RPOCs to meet "RPOC 4: Must support continuous monitoring".
The Anchore Federal UI provides dashboards summarizing vulnerabilities and your compliance posture across all your clusters. You can drill down into the details for an individual cluster or namespace and filter the dashboard. For example, selecting only high and critical vulnerabilities will only show the clusters and namespaces with those vulnerabilities.
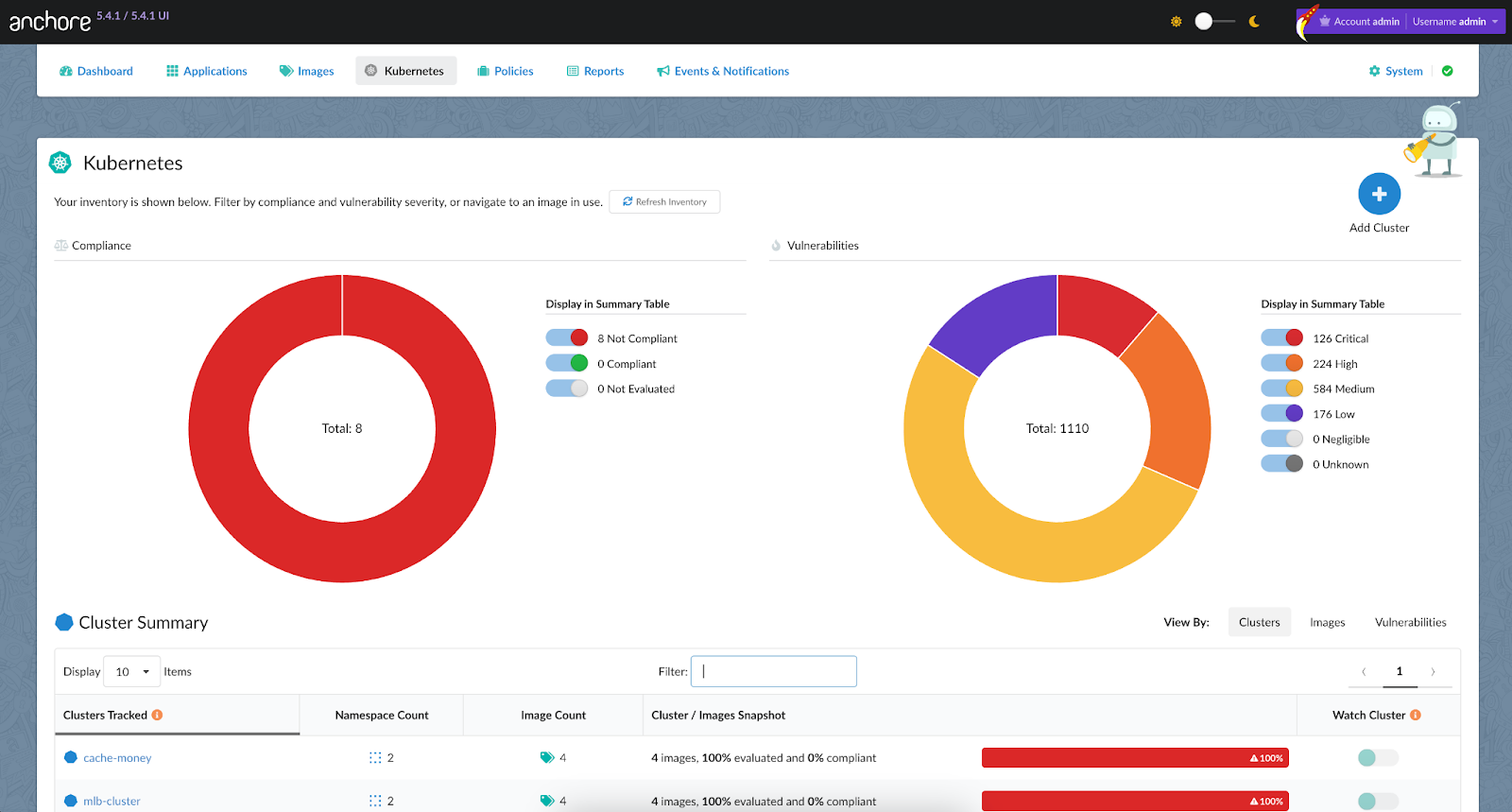
If a zero-day or new vulnerability arises, you can easily see the impacted clusters and containers to assess the blast radius.
Security gates that directly integrate into CI/CD pipeline
Anchore Federal automates required security gates for RPOCs and application owners (i.e., "RPOC 5: Must support the execution of Security Gates" and "APPO 9: Application(s) deployments must successfully pass through all Security Gates"). It integrates seamlessly into the CI/CD pipeline and the container registry, automatically generates SBOMs, and scans containers for vulnerabilities and secrets/keys (Gates 2, 3, and 4 in the RAISE 2.0 Implementation Guide).
Anchore's security gating feature is backed by a flexible policy engine that allows both RPOCs and application owners to collaborate on the security gates that need to be passed for any container going through a CI/CD pipeline and customized gates specific to the application. The Anchore Policy Engine accelerates the move to RAISE 2.0 by offering pre-configured policy packs, including NIST SP 800-53, and extensive docs for building custom policies. It is already used by DevSecOps platforms across the DON, including Black Pearl, Party Barge, and Lighthouse installations, and is ready to deploy in classified and air-gapped environments, including IL4 and IL6.
Production container inventory
On top of continuously monitoring production for vulnerabilities in containers, the anchore-k8s-inventory tool can be utilized to create an inventory of all containers in production which can then be queried by the container registry in order to meet "RPOC 15: Must retain every image that is currently deployed". This easily automates this requirement and keeps DON programs compliant with no additional manual work.
Single-pane-of-glass security dashboard
Anchore Federal maintains a complete repository of SBOMs, vulnerabilities, and policy evaluations. Dashboards and reports provide auditability that containers have met the necessary security gates to meet "RPOC 20: Must ensure that the CI/CD pipeline meets security gates".
Customizable vulnerability reporting and comprehensive dashboard
Anchore Federal comes equipped with a customizable report builder for regular vulnerability reporting and a vulnerability dashboard for ad hoc reviews. This ensures that RPOCs and application owners meet the "RPOC 24: Must provide vulnerability reports and/or vulnerability dashboards for Application Owner review" requirement.
Aggregated vulnerability reporting
Not only can Anchore Federal generate application specific reporting, it can provide aggregated reporting for vulnerabilities for all applications and containers on the DPOC. This is vital functionality for meeting the "QREV 6: Consolidated vulnerabilities report of all applications deployed, via the RAISE process" requirement.
Generate and store security artifacts
Anchore Federal both generates and stores security artifacts from the entire CI/CD pipeline. This meets the software supply chain security requirements of "QREV 7: Application Deployment Artifacts". Specifically this includes, SBOMs (i.e., dependency reports), container security scans, SRG/STIG scans.
Anchore Federal produces a number of the required reports, including STIG results, container security scan reports, and SBOMs, along with pass/fail reports of policy controls.
STIG results are generated by Anchore's Static STIG Checker tool. This automates STIG scanning and makes STIG compliance a breeze.
Remediation recommendations and automated allowlists
RAISE 2.0 requires that Application Owners remediate or mitigate all vulnerabilities with a severity of high or above within 21 calendar days. Anchore Federal helps speed remediation efforts to meet the 21-day deadline. It suggests recommended fixes and includes an Action Workbench where security reviewers can specify an Action Plan detailing what developers should do to remediate each vulnerability.
Anchore Federal also provides time-based allowlists to enforce the 21-day timeline. With the assistance of remediation recommendations and automated allowlists, application owners knows that their applications are always in compliance with "APPO 7: Must review and remediate, or mitigate, all findings listed in the vulnerabilities report per the timelines defined within this guide".
Automate STIG checks in CI/CD pipeline
The RPOC ISSM and the Application Owner must work together to determine what SRGs and STIGs to implement. Anchore’s Static STIG Checker tool automates STIG checks on Kubernetes environments and then uploads the results to Anchore Federal through a compliance API. That allows users to leverage additional functionality like reporting and correlating the runtime environment to images that have been analyzed.
This automated workflow specifically addresses the "APPO 10: Must provide and continuously maintain a complete Security Requirements Guide (SRG) and Security Technical Implementation Guide (STIG)" requirement.
Getting to RAISE 2.0 with Anchore Federal
Anchore Federal is a complete software supply chain security solution that gets RPOCs and application owners to RAISE 2.0 faster and easier. It is already proven in many Navy programs and across the DoD. With Anchore Federal you can:
- Automate RAISE requirements
- Meet required security gates
- Generate recurring reports
- Integrate with existing DSOPs
Anchore Federal was designed specifically to automate compliance with Federal and Department of Defense (DoD) compliance standards (e.g., RAISE, cATO, NIST SSDF, NIST 800-53, etc.) for application owners and DSOPs that would rather utilize a turnkey solution to software supply chain security rather than DIY a solution. The easiest way to achieve RAISE 2.0 is by adopting a DoD software factory which is the general version of the Navy's RPOC.
If you're interested to learn more about how Anchore can help your organization embed DevSecOps tooling and principles into your software development process, click below to read our white paper.