Container Security
Container security for a safer software supply chain.
Identify and remediate container security risks, and monitor post-deployment for new vulnerabilities.
Benefits
Continuous vulnerability scanning.
Automate vulnerability scans at each step in the development lifecycle, including source code repositories, CI/CD pipelines, container registries, and Kubernetes platforms. Identify vulnerabilities, malware, secrets, and security risks.
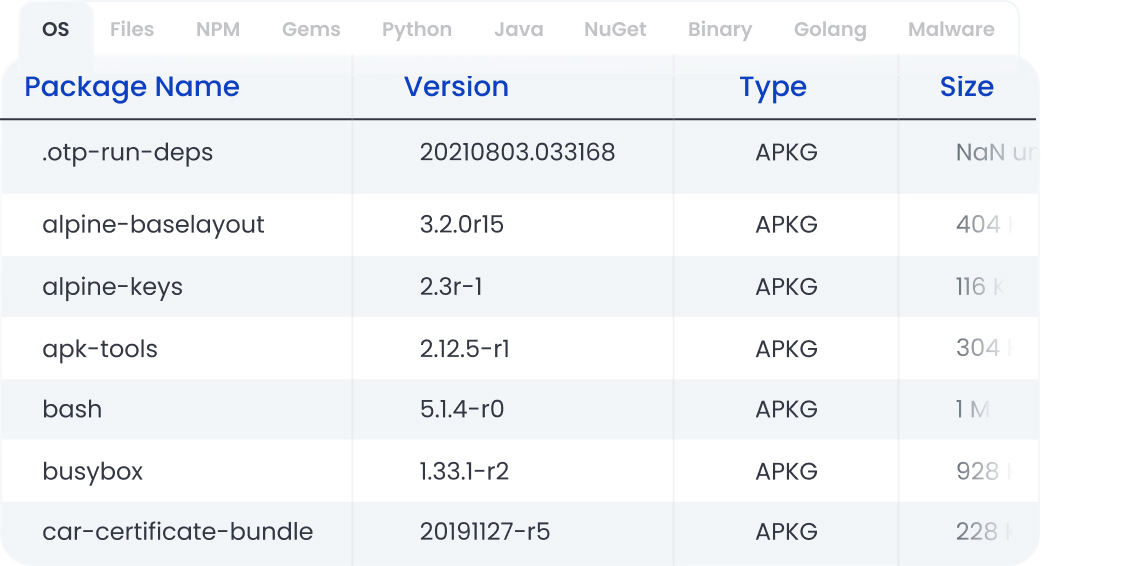
Use SBOMs to monitor risk.
Generate, store, analyze, and monitor SBOMs across the application lifecycle to identify software dependencies and get notified of vulnerabilities, even those that arise post-deployment.
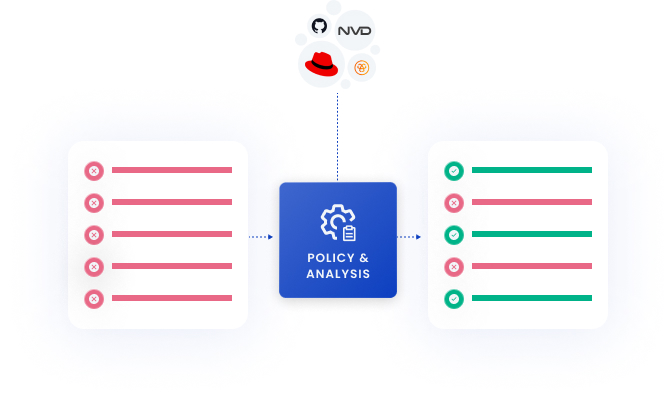
Fewer false positives.
Put more time into fixing urgent vulnerabilities and less time into chasing down false positives with Anchore’s unparalleled signal-to-noise ratio. Prioritize vulnerabilities based on severity and available fix; use allowlists to prevent unnecessary alerts; and use corrections to improve vulnerability results.
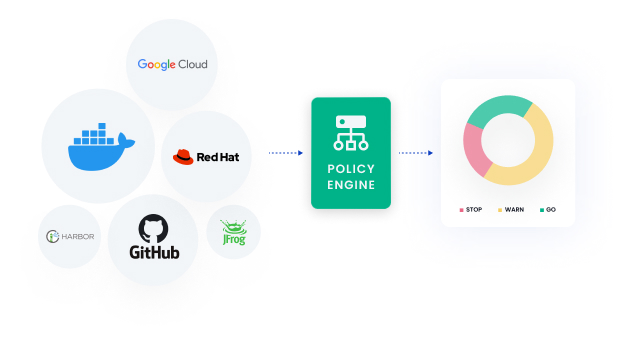
Simplify policy enforcement.
Identify container images that are out of compliance using flexible policies that flag problems. Meet compliance standards with out-of-the-box policy packs. Provide security teams with compliance reporting and implement policy gates to stop insecure code from reaching production.
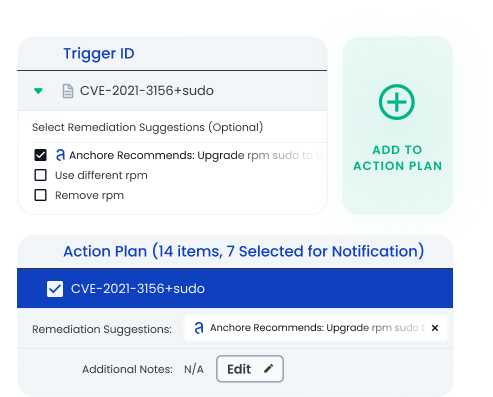
Quicker, easier remediation.
Reduce the time to remediate issues by shifting security scans earlier in the development process. Get remediation recommendations that identify updated versions. Automate remediation workflows to generate JIRA tickets or notifications vis Slack or other tools.
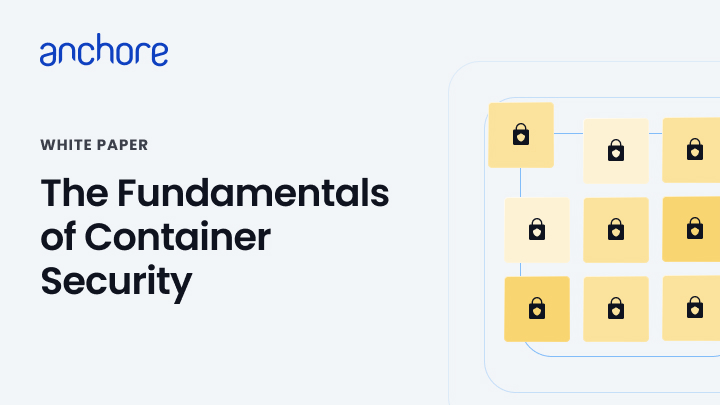
How container security works in Anchore.
Inspect and secure workloads across the entire software supply chain
Integrate with your existing toolchain.

























Related resources.
Speak with our security experts
Learn how Anchore’s SBOM-powered platform can help secure your software supply chain.